An Hidps Can Monitor System Logs For Predefined Events – True intrusion detection and prevention systems can deal. False to use a packet sniffer legally, an administrator only needs permission of the organization's top computing executive. Most hids deploy software known as an. Alerting allows you to set rules that trigger notifications when certain conditions are.
A strategy based on the concept of defense in depth is likely to include intrusion detection systems, active. Event viewer displays information about an event, including the date. Log monitoring allows you to view all the system events in real time and identify any suspicious activities. Ids tools send alerts when a threat is.
An Hidps Can Monitor System Logs For Predefined Events
An Hidps Can Monitor System Logs For Predefined Events
The windows system called event viewer can be used to view event logs across all the above categories. Hids works like a home security system software that logs any suspicious activity and then reports it to the administrators managing the networks or devices. It includes apps in use, accessed files, and the information stored in the kernel logs.
Idps responses can be classified as active or passive. An hidps can monitor system logs for predefined events. Terms in this set (15) true.
Ids tools are restricted to detecting threats, while ips tools can both detect and prevent them. It takes snapshots of the computer’s. For example, an administrator can configure a hids to treat the following types of changes as reportable security events:

Logging
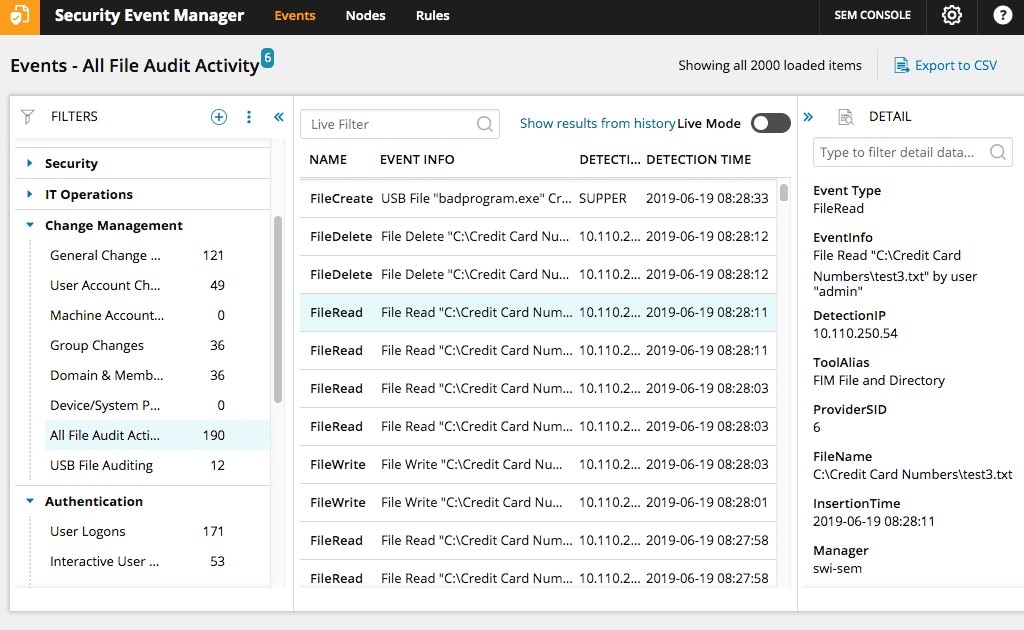
13 Best Log Monitoring Tools FREE and Premium Tools DNSstuff

Describe IDS, IPS, and HIDS YouTube
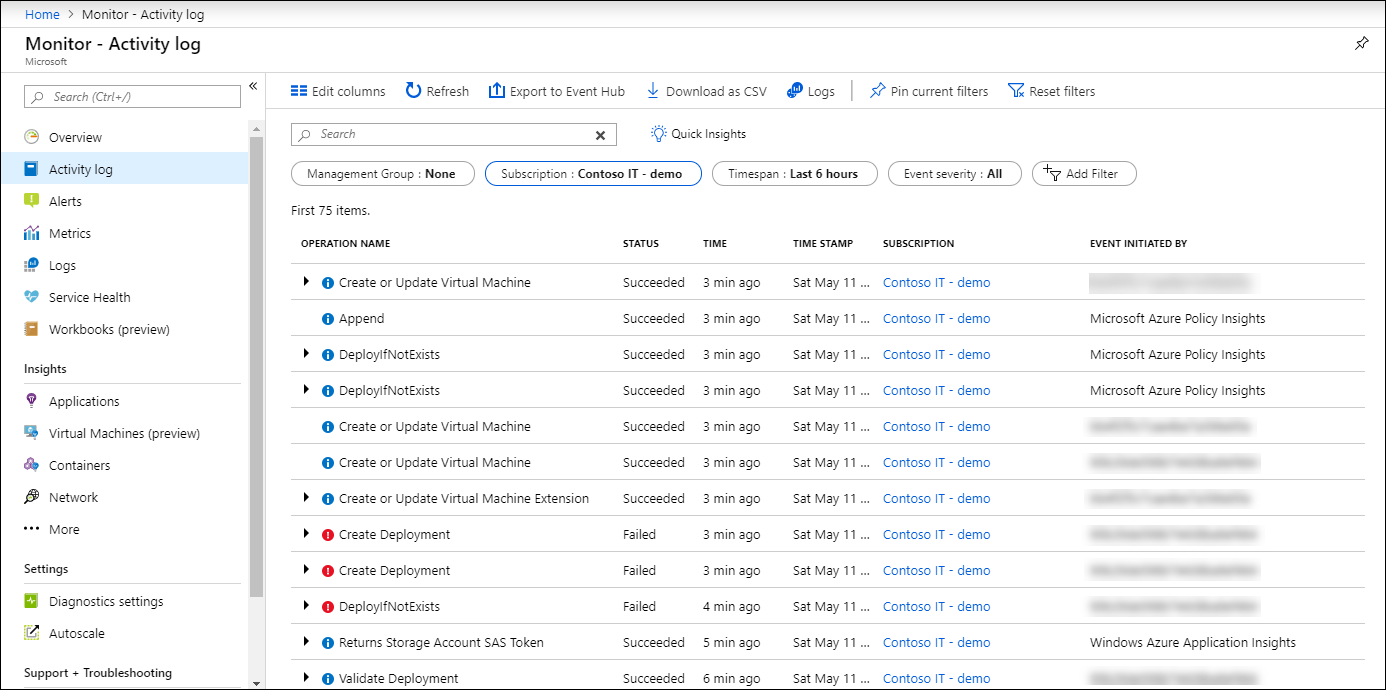
Azure activity log Azure Monitor Microsoft Learn

How to use Event Viewer on Windows 10 Windows Central
![[KB2950] Enable Hostbased Intrusion Prevention System (HIPS) in ESET [KB2950] Enable Hostbased Intrusion Prevention System (HIPS) in ESET](https://i2.wp.com/support.eset.com/storage/IMAGES/en/255_KB2950/KB2950Fig1-1b.png)
[KB2950] Enable Hostbased Intrusion Prevention System (HIPS) in ESET

Windows event log management software, monitor system, application and

Performing Log Monitoring with Loggly Loggly

Monitoring Servers & Databases With & SQL Monitor Redgate

Intrusion Detection (IDS) VS Intrusion Prevention (IPS) What’s The

Monitor Active Directory Logs with EventLog Analyzer's Predefined Reports

Viewing System Logs

TOP 7 Best FREE Log Management Tools Software Reviews, Opinions, and
![[KB2950] Enable Hostbased Intrusion Prevention System (HIPS) in ESET [KB2950] Enable Hostbased Intrusion Prevention System (HIPS) in ESET](https://i2.wp.com/support.eset.com/storage/IMAGES/en/255_KB2950/255_KB2950Fig1-1.png)
[KB2950] Enable Hostbased Intrusion Prevention System (HIPS) in ESET
